A known security hole in the networking protocol used by cellphone providers around the world played a key role in a recent string of attacks that drained bank customer accounts, according to a report published Wednesday.
The unidentified attackers exploited weaknesses in Signalling System No. 7, a telephony signaling language that more than 800 telecommunications companies around the world use to ensure their networks interoperate. SS7, as the protocol is known, makes it possible for a person in one country to send text messages to someone in another country. It also allows phone calls to go uninterrupted when the caller is traveling on a train.The same functionality can be used to eavesdrop on conversations, track geographic whereabouts, or intercept text messages. Security researchers demonstrated this dark side of SS7 last year when they stalked US Representative Ted Lieu using nothing more than his 10-digit cell phone number and access to an SS7 network.
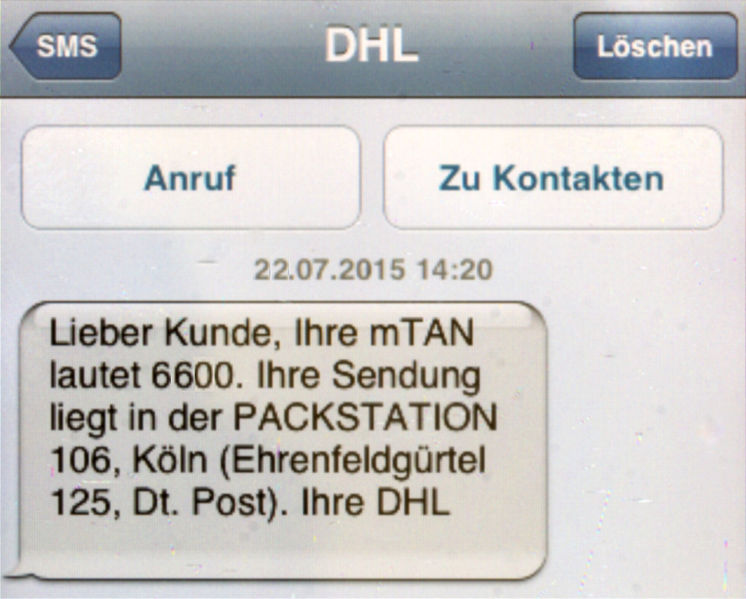
In January, thieves exploited SS7 weaknesses to bypass two-factor authentication banks used to prevent unauthorized withdrawals from online accounts, the German-based newspaper Süddeutsche Zeitung reported. Specifically, the attackers used SS7 to redirect the text messages the banks used to send one-time passwords. Instead of being delivered to the phones of designated account holders, the text messages were diverted to numbers controlled by the attackers. The attackers then used the mTANs—short for "mobile transaction authentication numbers"—to transfer money out of the accounts.
The interception of the mTANs came only after attackers had compromised bank accounts using traditional bank-fraud trojans. These trojans infect account holders' computers and steal the passwords used to log in to bank accounts. From there, attackers could view available balances, but they were prevented from making transfers without the one-time password the bank sent as a text message. In the past, attackers have obtained mTANs by obtaining a duplicate SIM card that allows them to take control of the bank customer's phone number. SS7-facilitated compromises, by contrast, can be done remotely on a much larger quantity of phone numbers.
Telecom confirms SS7 abuse
"Criminals carried out an attack from a network of a foreign mobile network operator in the middle of January," a representative with Germany's O2 Telefonica told a Süddeutsche Zeitung reporter. "The attack redirected incoming SMS messages for selected German customers to the attackers." The unidentified foreign network provider has since been blocked, and affected customers were informed of the breach.
The potential for widespread abuse of SS7 first came to light in 2008, but awareness remained largely limited. In 2014, The Washington Post explained how it was becoming increasingly easy for SS7 to be exploited by both government intelligence agencies and non-state actors. Last year, US TV news program 60 Minutes demonstrated the attack on Representative Lieu's number.
A few hours after this post went live, Lieu issued the following statement:
Everyone's accounts protected by text-based two-factor authentication, such as bank accounts, are potentially at risk until the FCC and telecom industry fix the devastating SS7 security flaw. Both the FCC and telecom industry have been aware that hackers can acquire our text messages and phone conversations just knowing our cell phone number. It is unacceptable the FCC and telecom industry have not acted sooner to protect our privacy and financial security. I urge the Republican-controlled Congress to hold immediate hearings on this issue.
Despite the growing awareness, Wednesday's report makes clear that real-world attacks remain—or at least until recently remained—feasible in industrialized countries. The attacks underscore the inherent insecurity and lack of privacy in the global telephone network. In August, Lieu called on the FCC to fix the SS7 flaws that make such attacks possible. It could take years to fully secure the system given the size of the global network and the number of telecoms that use it. When possible, people should use Open Whisper Systems' Signal app to encrypt text messages and phone calls sent or made to other people who use the app.
Wednesday's report also underscores the risks of relying on text messages for two-factor authentication. (Last year, the National Institute for Standards and technology proposed doing away with SMS and voice calls for so-called out-of-band verifiers.) Whenever possible, people should also avoid using text messages to receive one-time passwords. Instead, they should rely on cryptographically based security keys as a second authentication factor. When that's not possible, they should use a dedicated smartphone app such as Duo Security or Google Authenticator.Post updated at 5:08 PM California time to add comment from Lieu.
reader comments
116