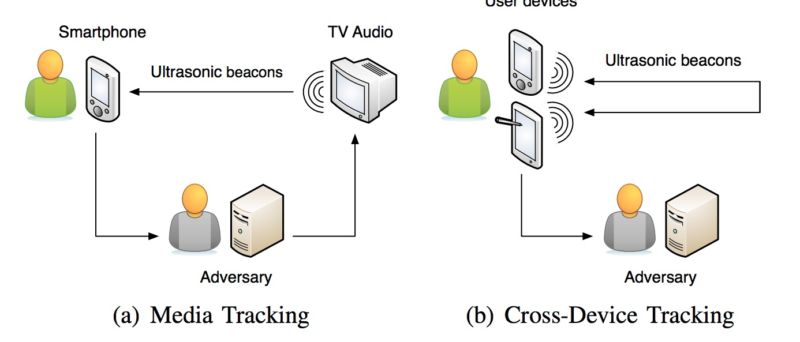
Almost a year after app developer SilverPush vowed to kill its privacy-threatening software that used inaudible sound embedded into TV commercials to covertly track phone users, the technology is more popular than ever, with more than 200 Android apps that have been downloaded millions of times from the official Google Play market, according to a recently published research paper.
As of January, there were 234 Android apps that were created using SilverPush's publicly available software developer kit, according to the paper, which was published by researchers from Technische Universitat Braunschweig in Germany. That represents a dramatic increase in the number of Android apps known to use the creepy audio tracking scheme. In April 2015, there were only five such apps.The apps silently listen for ultrasonic sounds that marketers use as high-tech beacons to indicate when a phone user is viewing a TV commercial or other type of targeted audio. A representative sample of just five of the 234 apps have been downloaded from 2.25 million to 11.1 million times, according to the researchers, citing official Google Play figures. None of them discloses the tracking capabilities in their privacy policies.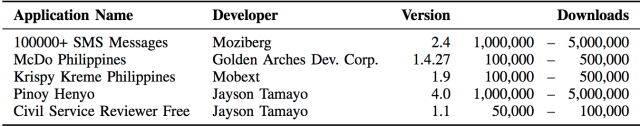
"The example of SilverPush highlights how easily this technology can be used to spy on users," Erwin Quiring, one of the researchers, wrote in an e-mail. "In this way, they can track the TV viewing habits of users precisely even with traditional broadcasting technologies. In our research paper, we identified three further privacy risks that can occur with this technology, e.g., tracking locations, behavior devices, and even the de-anonymization of Tor users."
SilverPush founder Hitesh Chawla said the finding surprised him because his company abandoned the ad-tracking business in late 2015.
"We respect consumer privacy and would not want to build our business foundation where the privacy is questionable," he told Ars. "Even when we were live, our SDK was not present in more than 10 to 12 apps. So there is no chance that our presence in 234 apps is possible. Every time a new handset gets activated with our SDK, we get a ping on our server. We have not received any activation for six months now."
The researchers, however, stand by the figure and say that all 234 apps positively contain the SilverPush SDK. That means phones that have the apps installed are silently listening for ultrasonic sounds without the knowledge or consent of their owners. While the researchers were unable to find any beacons in TV audio, they compared successful detections with finding a needle in a hay stack and left open the possibility such beacons are actively being embedded into TV audio. Even if they're not actively used, the growth in apps signals the practice could become widespread in the near future. The results were drawn from a corpus of 1.3 million Android apps submitted to the VirusTotal file scanning service, and as a result they shed no light on how prevalent audio beaconing may be in apps running on iOS devices from Apple.
A Google representative said that the privacy policies enforced on all apps available in the Play market require developers to "comprehensively disclose how an app collects, uses and shares user data, including the types of parties with whom it's shared." The representative didn't respond to a follow-up question asking why none of five apps cited in the research findings disclosed the SilverPush functions. At the time this post went live, all five apps remained available in Play.
The beacons are frequencies from 18kHz to 20kHz, a range that is inaudible to most humans but can be reliably detected by most phone microphones. By embedding them into audio, marketers can track the whereabouts of shoppers as they move throughout a large department store. Promoters using other companies' audio-beacon technologies can also use them to push ads or coupons to people who are near a certain store or service. The researchers said two services—Shopkick and Lisnr—use ultrasonic beaconing for legitimate purposes such as these, and they disclose the tracking prominently.
The tracking can also be used for purposes that are decidedly less ethical. Advertisers, for example, may use the beacons with no disclosure at all to measure how often a particular TV ad is viewed. The technology can also be covertly used to perform cross-device tracking that allows marketers to tie a single person to the multiple media devices she uses. The researchers said the beacons could similarly be used to identify people using the Tor anonymity service.
This paper was published at the 2nd annual IEEE European Symposium on Security and Privacy and was presented last week in Paris, France. In the paper, the researchers wrote:
In summary, an adversary is able to obtain a detailed, comprehensive user profile by creating an ultrasonic side channel between the mobile device and an audio sender. Our case study on three commercial ultrasonic tracking technologies reveals that the outlined tracking mechanisms are not a theoretical threat, but actively deployed (e.g. Shopkick and Lisnr) or at least in the process of being deployed (e.g. SilverPush).
The 234 detected apps contain SilverPush functionality alongside their normal content. Many were developed for large companies such as McDonald's and Krispy Kreme. At the moment, there are a limited set of countermeasures to prevent such tracking. For people using version 6.0 or higher, they can disable an app's access to the device microphone. This is a good practice to follow in general, although it may prevent useful features such as voice-to-text from working. It's also a good idea to limit the number of installed apps.
Longer term, antivirus providers may be able to add features that detect the tracking during routine scans of installed apps. Another long-term solution is to lobby government regulators, Google, Apple, and other companies to strictly enforce clear and prominent disclosure of all ultrasonic-based tracking.
Post updated to add sentences in last paragraph about Android app permissions.
Listing image by Takayuki Miki
reader comments
222